Data backups are becoming an operational necessity for small to medium-sized businesses (SMBs). SMBs are an attractive target for cybercrime since they often lack the resources to defend against new ransomware strains and sophisticated advanced persistent threats (APTs).
Data loss, whether from human error or cybercrime, results in costly downtime. Managed Service Providers (MSPs) report that the average cost of downtime due to ransomware has increased from $46,800 to $274,200. The inflated cost of downtime is a bill most SMBs cannot afford. According to the Small Business Administration (SBA), 25% of small businesses never recover from a data loss.
Every organization should have a business continuity and disaster recovery (BCDR) plan — and a key component of that plan should include data backup software. Before implementing a data backup plan, businesses need to determine what type of backup is the right choice for their business.
3 Main Types of Data Backup Strategies
Let’s review the advantages and disadvantages of the main types of backup methods - full, differential, and incremental - to ensure you choose the optimal data backup strategy for your organization’s needs.
1. Full Data Backups
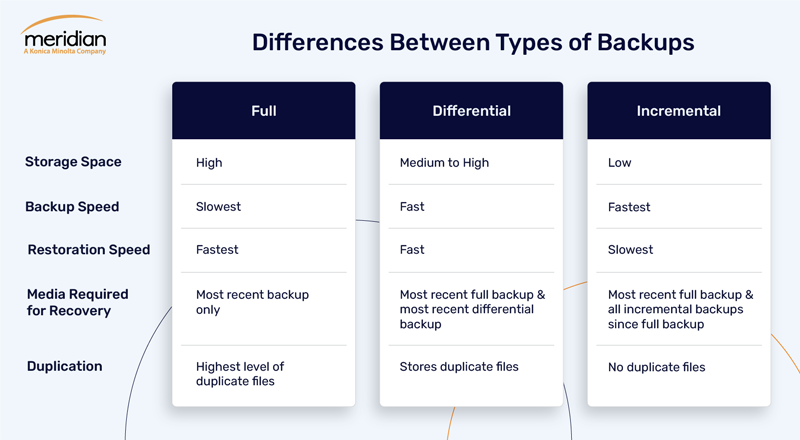
As the name implies, a full data backup refers to a complete copy of all data, including files and folders, regardless of any previous backups or circumstances. The entire data set is backed up and stored either onsite, at another location, or both. Full backups are the quickest to restore since all files are contained in the same backup set.
Full backups typically provide the best protection against critical data loss, but they are often conducted periodically on a predetermined schedule because of the time and expense involved. However, any good backup plan should include a full data backup, at least once, as a foundation.
A full data backup is generally the easiest to perform but not necessarily the simplest to administer. Here are a few disadvantages to keep in mind:
- Uses the most storage out of each method
- Requires substantial network bandwidth
- Often needs additional hardware if the data set is large
- Considerable implementation time, depending on the size of the business
The other two backup types — differential and incremental — are offshoots of a full data backup in that they work with a full data backup. The differential and incremental backups are similar and have some subtle yet important differences.
2. Differential Data Backup
Differential backups start with a full backup to store all files. Then, differential backups are run to include all the changes made to files and folders since the last full backup. A differential backup is cumulative. Therefore, a full and a differential backup together include all the files in your data set, changed and unchanged.
Companies can restore data faster than a full backup since differential backups require only two components: the initial full backup and the most recent differential backup. While differential backups enable a faster restoration time over incremental backups, they need more space and use much more network bandwidth.
3. Incremental Data Backup
Similar to differential backups, incremental backups start with a full backup to store all files. Then, the subsequent backups only store additions and alterations made to the previous backup or the most recent incremental backup. While a differential backup contains all data since the last full backup, an incremental backup includes only the data which has changed since any previous backup.
Since incremental backups only store the changes (increments), they require the least storage space, enabling accelerated backup speeds. However, they have the most time-consuming restoration process. To restore a full system, a company first needs to restore the latest full backup and then restore each incremental backup in order. Complete restoration becomes increasingly difficult or impossible if one incremental backup is lost, damaged, or stolen.
Choosing the Right Data Backup Method for Your Business
Businesses need to have a backup strategy as cybersecurity risks continue to grow in frequency and severity. Whether internal documents, photos, video files, or confidential information, your company needs the agility to quickly and efficiently restore business-critical data with minimal downtime.
Choosing the data backup type that is right for your company depends on several factors, including:
- How much data are you backing up?
- How much time can your organization devote to the process?
- How quickly will you need to recover lost data in case of a disaster?
- What operating system(s) and software programs does your business use?
Businesses should consult a data protection and recovery specialist for guidance throughout the selection process. To determine the data backup type that is right for your business, an experienced managed IT service provider will conduct an IT assessment and provide in-depth answers to these and many other data backup, disaster recovery, and business continuity questions.
Editor’s Note: This post was originally published on August 26, 2015, and has been updated for accuracy and current best practices.




